In the digital era, organizations face a constant barrage of cyber threats that can exploit vulnerabilities, disrupt operations, and compromise sensitive data. Rather than questioning if a breach will occur, organizations must prepare for when it happens. Rapid and effective mitigation is only achievable through a thoroughly crafted incident response plan. A well-prepared security incident response team is the axis around which successful incident mitigation revolves, ensuring that technical, legal, and communication actions are swiftly aligned. Without a comprehensive action plan, the consequences of a cyberattack can be far-reaching: financial losses, regulatory fines, business disruption, and lasting reputational harm. An incident response plan (IRP) isn’t just a checklist—it’s a living document that requires constant attention and adjustment. Committing the right resources and empowering response teams lays the groundwork for organizational resilience in the face of evolving cyberthreats. The stakes are higher than ever. A recent Accenture report underscores the growing financial burden: companies caught unprepared for cyberattacks can face average losses exceeding $380,000 per incident. With threats growing in scale and sophistication, proactive preparation is the single most influential factor in reducing the fallout from a breach. This article explores the critical elements of a robust incident response plan, outlining essential processes, training strategies, technologies, and the importance of ongoing collaborative improvements. Implementing and refining an IRP is not only about damage control but about fortifying your organization for the future.
Understanding the Importance of an Incident Response Plan
Cyber incidents are inevitable in today’s hyperconnected landscape. From ransomware attacks to insider threats, a surge of new risks has underscored the critical need for detailed, flexible response playbooks. An IRP protects more than IT assets—it preserves business continuity, protects client trust, and meets regulatory expectations. An agile and adaptive IRP can mean the difference between minor disruption and catastrophic loss. Building resilience is about more than simply patching up after an incident. It means considering not just technical solutions but also human and operational factors.
Key Components of a Resilient Incident Response Plan
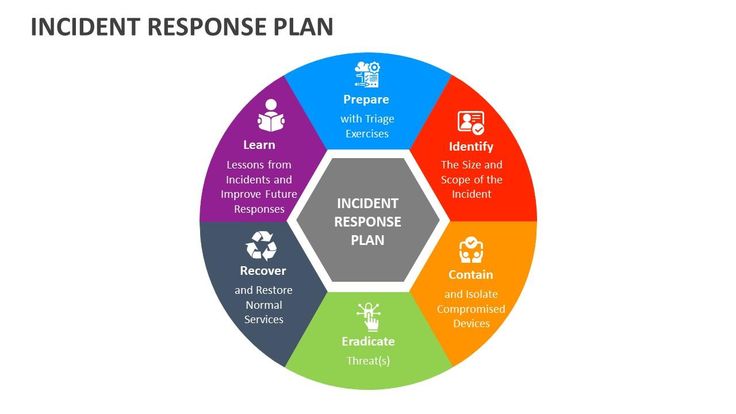
An effective IRP typically includes these critical phases:
- Preparation: Establishing response policies, communication protocols, and resource allocation ensures readiness before a crisis hits. This includes conducting risk assessments, clarifying roles, and assembling response teams.
- Identification: Early detection leverages monitoring tools, threat intelligence, and employee vigilance to detect potential incidents and assess their scope.
- Containment: Quickly isolating impacted systems is vital for preventing further compromise while preserving forensic evidence for investigation.
- Eradication: Removing malware, closing vulnerabilities, and verifying system integrity eliminates the root cause to prevent recurrence.
- Recovery: Safely restoring operations, ensuring systems are fully patched, and monitoring for lingering issues are keys to resilience post-incident.
- Lessons Learned: Documenting the incident and analyzing response gaps transforms each event into an opportunity for organizational growth and improvement.
Establishing an Incident Response Team
A dedicated incident response team (IRT) should represent departments across IT, legal, compliance, HR, communications, and C-suite leadership. These cross-functional teams can communicate and collaborate rapidly, addressing technical and business priorities in tandem. Clear role definitions and a transparent chain of command minimize confusion, ensuring swift, unified action during crises. The IRT should also maintain up-to-date contact lists, escalation procedures, and designated spokespersons to ensure internal and external communications are accurate and coordinated—even amid chaos.
Developing Incident Response Playbooks
Incident response playbooks go beyond generic plans by mapping specific scenario-based actions. Whether facing a ransomware attack, phishing campaign, or data breach, tailored step-by-step guides outline the technical, legal, regulatory, and communication steps to follow at each stage. Playbooks should include notification templates, checklists, escalation paths, and an incident documentation process. Regularly reviewing and updating playbooks ensures they stay relevant and practical as threats shift and the organization evolves.
Conducting Regular Training and Simulations
Practical, hands-on experience is the best test of preparedness. Regular training and cyberattack simulations enhance team competence, highlight process gaps, and build muscle memory for efficient decision-making under stress.
Leveraging Technology for Incident Detection and Response
Advanced technology is a force multiplier in incident response. Security Information and Event Management (SIEM) systems, endpoint detection and response (EDR) tools, and automation platforms greatly improve threat visibility and accelerate response times. Automated workflows and artificial intelligence can speed up detection and remediation, freeing up human responders for deeper analysis and decision-making. Selecting, integrating, and continuously tuning these tools maximizes their effectiveness and complements well-trained response teams.
Collaborating with External Partners
No organization stands alone against cyberthreats. Building established relationships with law enforcement, industry peers, cybersecurity vendors, and incident response consultants brings critical outside expertise and support during or after an incident. External partners can help with forensic investigations, legal compliance guidance, and up-to-date threat intelligence. Cooperative information sharing also strengthens collective defense across sectors and industries.
Continuous Improvement and Post-Incident Analysis
Every cyber incident is an opportunity for learning. Conducting a structured “lessons learned” review after an event reveals gaps, strengths, and actionable steps for improvement. Updates to the IRP, training programs, and detection technologies should directly reflect findings from these sessions. Treating incident response as a strategic business capability sets leading organizations apart. Continuous investment in people, process, and technology creates a virtuous cycle of improved resilience and preparedness, ensuring long-term protection against ever-changing cyber risks. By proactively developing, testing, and refining your organization’s incident response plan, you not only reduce the immediate impact of threats but also position your business to thrive in the face of tomorrow’s digital challenges.